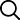
How to implement NFC label anti-counterfeiting?
Release Time:
2020-08-27
The unique ID number burned by the factory with a length of 7 bytes Writing data can be burned to death, no one can write, only read 32-bit password that prevents unauthorized write operations
About the security of the NFC tag chip itself
The unique ID number burned by the factory with a length of 7 bytes
Writing data can be burned to death, no one can write, only read
32-bit password that prevents unauthorized write operations
About Encryption of NFC Tags
The content of NFC tags can be read arbitrarily, and there is no permission setting mechanism
If you have to use NFC tags, you can encrypt the tag content (although you can read it arbitrarily, but what you read is ciphertext). If the ciphertext content needs to be decrypted in the end, you can use AES, RSA and other algorithms to encrypt it. For decryption, you can use the algorithm of the SHA family;
Other types of cards can be used, such as Mifare classic series cards (MIFARE Classic :: NXP NXP Semiconductors), Mifare DESFire EV1 series cards (MIFARE DESFire :: NXP NXP Semiconductors) and other cards; they authorize access to the card fans through secret keys (keyA/keyB) area content. (This solution has two problems, one is mobile phone compatibility, and the other is cost, which is more expensive)
How to make an NFC tag an anti-counterfeit tag
Obtain a ciphertext by using the unique ID number burned out of the factory through an asymmetric encryption algorithm
Store the ciphertext in the NFC tag data area
Verify the device or software, read the unique ID number, the software itself calculates the ciphertext or returns to the background server to calculate the ciphertext
Compare whether the ciphertext matches and judge the authenticity
NFC tag anti-counterfeiting writing process

NFC tag anti-counterfeiting verification process
How to counterfeit this NFC tag, where is the cost of counterfeiting
Unique ID number, there are only a handful of fabs in the world. Once a counterfeit NFC tag is found, you can immediately find the fab that produced the tag IC through the NFC tag. Just follow the vine.
The ciphertext obtained by the asymmetric encryption algorithm is irreversible. Even if the counterfeiter has the NFC tag with the ID number copied, there is no way to generate the ciphertext.
in conclusion
The unique ID number of the chip manufacturer and its own encryption algorithm are double-protected. Even if the uniqueness of the ID of the chip manufacturer is cracked, there is also your own private encryption protection, which can be described as double insurance.
Reprinted from NFC Home

Guangdong Joinet IOT Technology Co.,Ltd
Manufacturing Base:
Joinet Technology Park,No. 168 Tanlong North Road,Tanzhou Town,Zhongshan City,Guangdong Province,China
Pre Sales Hotline:19966308713 13823973022
Switchboard:0760-8663 0003 (transferred) 523
Pre Sales Email:sw@znaiot.com


Contact Us:
Looking forward to your call anytime